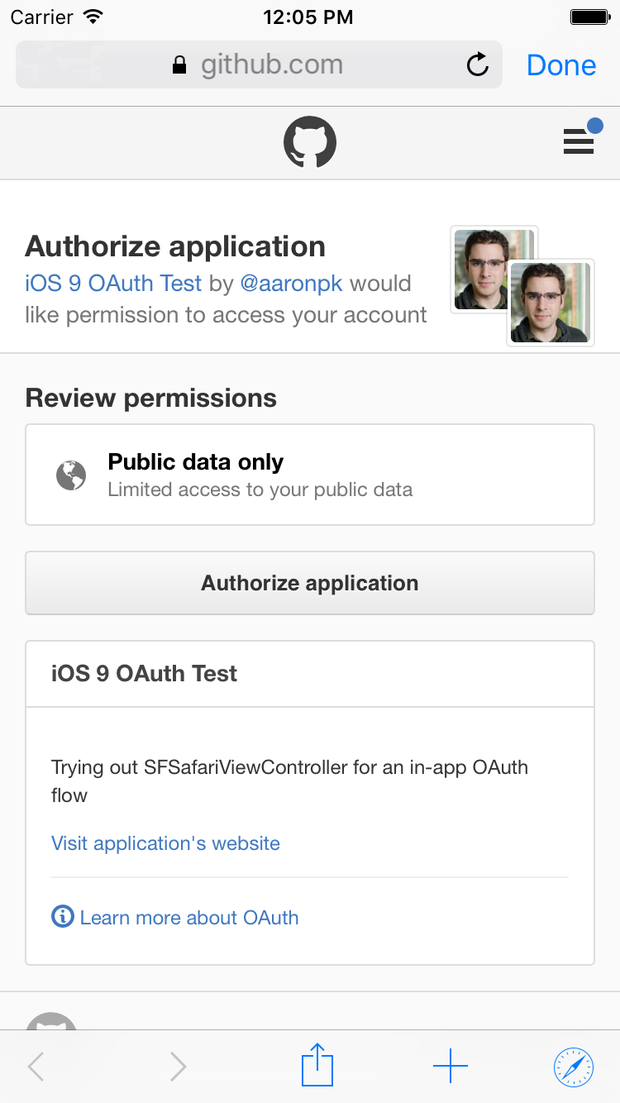
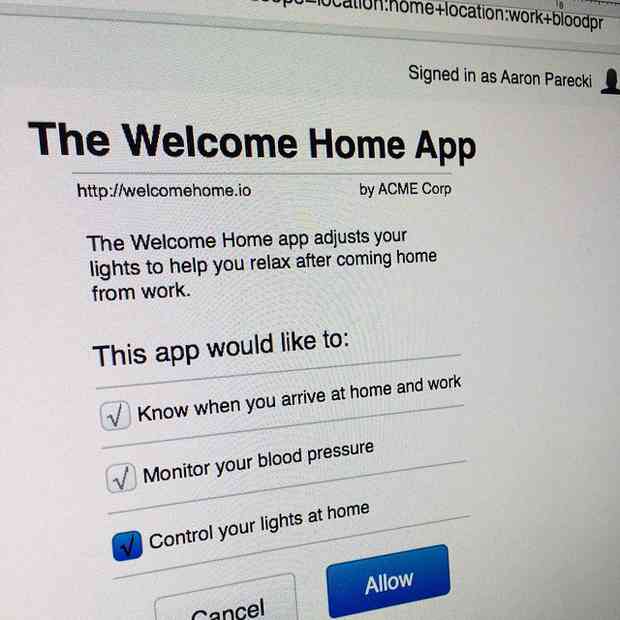
Hi, I'm Aaron Parecki. I write about OAuth here, and I give talks about OAuth 2.0. Below you'll find my recent posts about various OAuth-related things, including talks I'm giving. I've also written two community resources about OAuth:
OAuth 2.0 Simplified is a guide to OAuth 2.0 focused on writing clients that gives a clear overview of the spec at an introductory level.
In 2017, I published a longer version of this guide as a book, available on oauth.com as well as a print version. The book guides you through building an OAuth server, and covers many details that are not part of the spec. I published this book in conjunction with Okta.