WeChat ID
aaronpk_tv
-
-
-
-
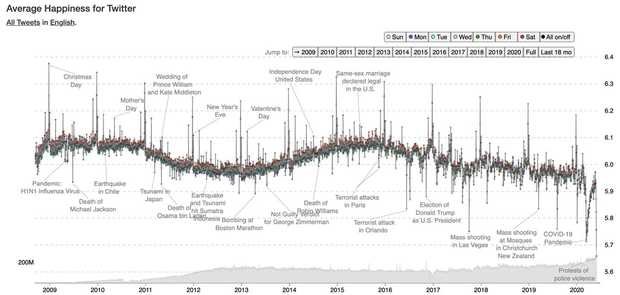
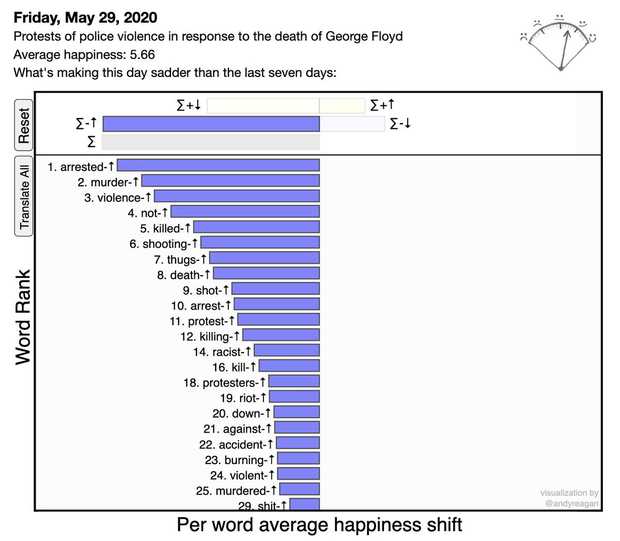
When writing headlines, use the active voice and clearly identify subjects. https://www.theverge.com/2020/5/31/21276044/police-violence-protest-george-floyd
-
This is a great illustration of how much space cars waste!
They say that up to 230 cars will be able to fit in the stadium to watch the movie. 230 cars in the whole damn stadium.
If this is the future, I don’t wanna be in it. https://www.miamiherald.com/miami-com/things-to-do/article243003896.html -
-
-
-
-
Fully agree to that 😀
Just looking also at examples like https://insomniasec.com/blog/auth0-jwt-validation-bypass or https://threatpost.com/microsoft-oauth-flaw-azure-takeover/150737/.
o/c they are different + very individual, but if already the big players have such issues, how much more can go wrong on RS side where devs are usually not Auth experts. -
-
-