WeChat ID
aaronpk_tv
-
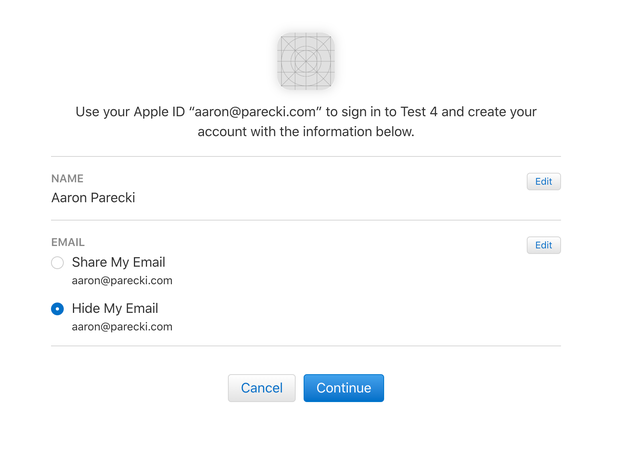
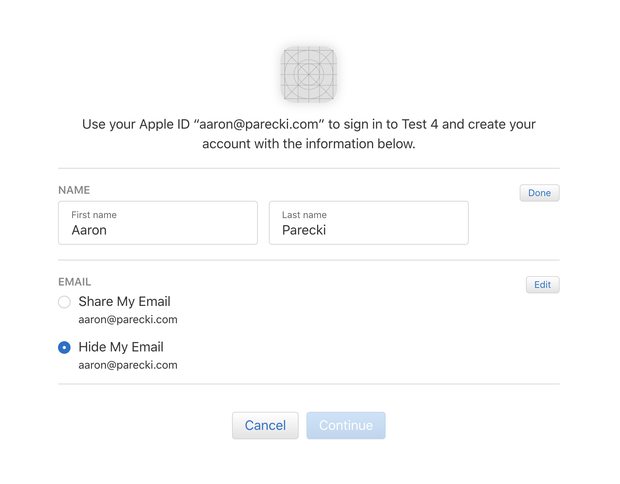
So @aaronpk actually provides an example of users being able to edit their names at least in the JS. This makes me feel MUCH MORE comfortable with it. https://twitter.com/aaronpk/status/1137149365120786432
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
Portland, Oregon • Thu, June 6, 2019 10:54amMore coffee