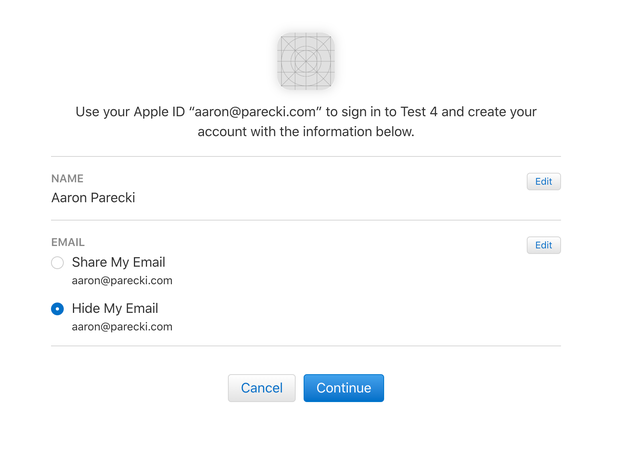
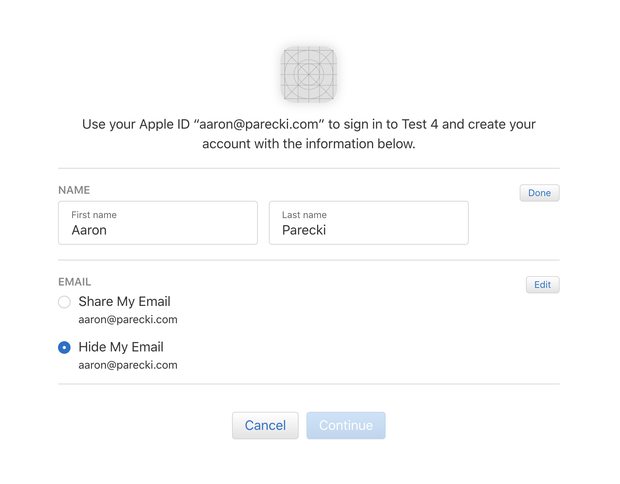
I'd like to self-host a single mailing list that is never going to have more than about 25 people on it. Is there a dead-simple thing (wayyy simpler than Mailman) that will just.... alias something like thelist@tinysubversions.com to CC 25 different email addresses?
It doesn't need a public or even private archive messages. It's just for a small group of friends who want to stay in touch.