Thursday, May 2, 2019
| taxi |
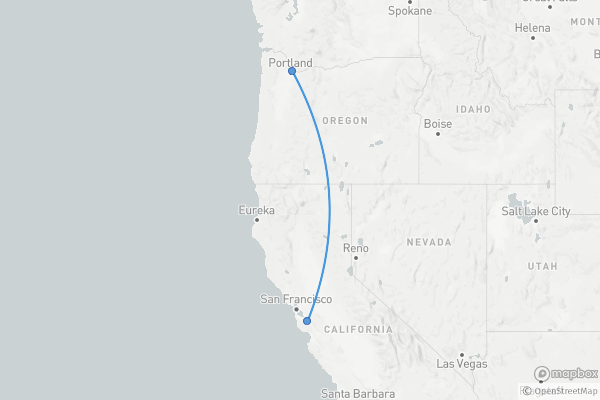
2 hr 17 min
|
| plane |
1 hr 36 min
|
| train |
23 min
|
|
646 miles
|
plane |
|
14.2 miles
|
taxi |
|
9 miles
|
train |
-
-
-
at Hotel VueMountain View, California • Thu, May 2, 2019 7:29am
-
-
Mountain View, California • Thu, May 2, 2019 7:54am
-
-
-
-
-
-
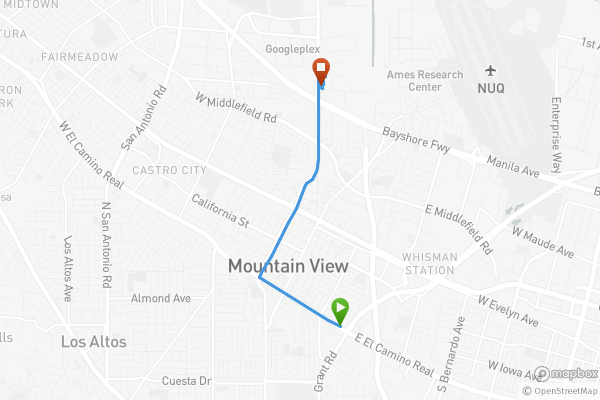
Taxi3.70miDistance102:40DurationStartEnd
-
-
-
-
-
-
-
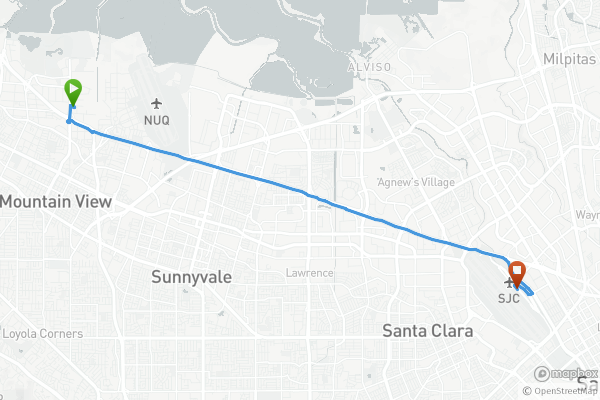
Taxi10.54miDistance34:47DurationStartEnd
-
San Jose, California • Thu, May 2, 2019 3:43pm
-
San Jose, California • Thu, May 2, 2019 3:48pm
-
San Jose, California • Thu, May 2, 2019 3:57pm
-
-
In @justin__richer’s #IIW “DIDn’t” session: Once more with feeling: Privacy is not secrecy; privacy is not encryption; privacy is context, control, choice, and respect.
-
At #IIW session on “Is #selfsovereignidentity really possible”, @xmlgrrl Eve Maler offers perhaps the most concise definition of of #privacy I’ve ever heard: “Privacy is context-controlled choice and respect.” Beautiful. And I believe actually possible with #SSI.

-
Biggest laugh at #IIW so far: when @justin__richer in his session on “Is #selfsovereignidentity really possible” turned to Dave Crocker and said that we can all blame him for the Internet not having #security built in from the start.

-
-
-
-
-
-
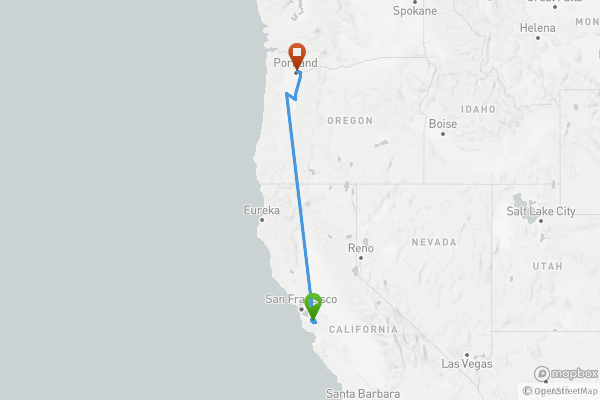
at Gate 27San Jose, California • Thu, May 2, 2019 5:20pm
-
Plane647.44miDistance96:01DurationStartEnd
-
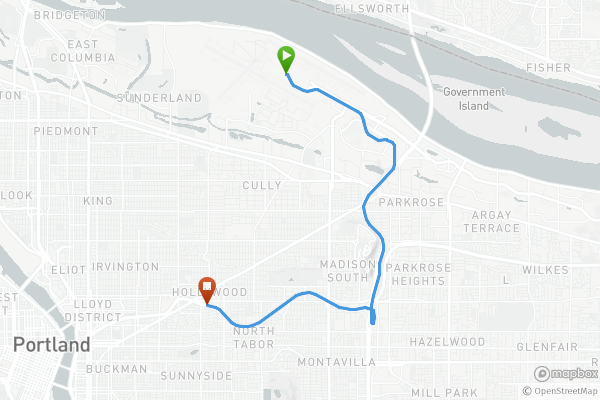
Train9.02miDistance23:19DurationStartEnd
-
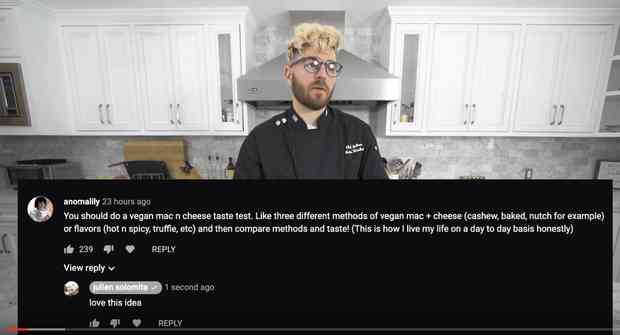
Just found out that @juliensolomita used my suggestion in his most recent video to do a mac + cheese tasteoff and I am STOKED. Because I love nothing more than some vegan mac. https://www.youtube.com/watch?v=EBv5A7NC2eI